Hi, in this Post you will get to know how to Create Virtual Machine in Microsoft Virtual PC
1. Open Virtual PC and click on New.
2. In the New Virtual Machine Wizard click Create a Virtual Machine.
3. In the Virtual Machine Name and Location click to browse to point to the location where you want to place your new VM. Note that the best location for the VM is on a separate disk and NOT on the same physical disk as your
4. In the Operating System window select your required guest operating system. Note the large list of Microsoft-based operating systems. If you plan to install a non-Microsoft OS then choose "Other".
5. In the Memory window note that Virtual PC tries its best to determine the recommended amount of RAM to allocate to the new Guest VM based upon your selection in the previous step. You can manually change that setting.
6. In the Virtual Hard Disk Options window click to select A New Virtual Hard Disk. If you've already created the hard disk in a different manner (read my "How to create a new Virtual Machine (Hyper-V) " article for more info), then select An Existing Hard Disk.
7. In the Virtual Hard Disk Location window browse to the location of the new hard disk, and give it a proper name. Try to be as specific as possible and try to place each VM in its own folder. You need to specify the size of the new virtual hard disk. Make sure you'll have enough space on it to install whatever OS that you want, and also plan for any additional software or services.
Note: Virtual PC uses dynamically expanding disks, meaning they start out as small .VHD files, but the VM itself "sees" them in their full size. As space is taken on the virtual hard disk by the VM, the size of the .VHD file increases.
10. When you're done click Finish. Your new VM is ready to boot.
Welcome to Information Technology Blog. You will get the troubleshooting and latest information related to Windows Servers , XP, Windows 7, Linux, Untangle, Anti-viruses, IIS, Browsers etc..
Thursday, December 30, 2010
Monday, December 27, 2010
Some PowerShell Commands
Some PowerShell Commands Every Windows Admin should Know
Almost all the newer Microsoft server products require PowerShell, and there are lots of management tasks that can't be accomplished without delving into the command line. As a Windows administrator, you need to be familiar with the basics of using PowerShell. Here are some commands to start with
1: Get-Help
The first PowerShell cmdlet every administrator should learn is Get-Help. You can use this command to get help with any other command. For example, if you want to know how the Get-Process command works, you can type:
Get-Help –Name Get-Process
And Windows will display the full command syntax.
You can also use Get-Help with individual nouns and verbs. For example, to find out all the commands you can use with the Get verb, type:
Get-Help –Name Get-*
2: Set-ExecutionPolicy
Although you can create and execute PowerShell scripts, Microsoft has disabled scripting by default in an effort to prevent malicious code from executing in a PowerShell environment. You can use the Set-ExecutionPolicy command to control the level of security surrounding PowerShell scripts. Four levels of security are available to you:
.
Restricted -- Restricted is the default execution policy and locks PowerShell down so that commands can be entered only interactively. PowerShell scripts are not allowed to run.
.
All Signed -- If the execution policy is set to All Signed then scripts will be allowed to run, but only if they are signed by a trusted publisher.
.
Remote Signed -- If the execution policy is set to Remote Signed, any PowerShell scripts that have been locally created will be allowed to run. Scripts created remotely are allowed to run only if they are signed by a trusted publisher.
.
Unrestricted -- As the name implies, Unrestricted removes all restrictions from the execution policy.
You can set an execution policy by entering the Set-ExecutionPolicy command followed by the name of the policy. For example, if you wanted to allow scripts to run in an unrestricted manner you could type:
Set-ExecutionPolicy Unrestricted
3: Get-ExecutionPolicy
If you're working on an unfamiliar server, you'll need to know what execution policy is in use before you attempt to run a script. You can find out by using the Get-ExecutionPolicy command.
4: Get-Service
The Get-Service command provides a list of all of the services that are installed on the system. If you are interested in a specific service you can append the –Name switch and the name of the service (wildcards are permitted) When you do, Windows will show you the service's state.
5: ConvertTo-HTML
PowerShell can provide a wealth of information about the system, but sometimes you need to do more than just view the information onscreen. Sometimes, it's helpful to create a report you can send to someone. One way of accomplishing this is by using the ConvertTo-HTML command.
To use this command, simply pipe the output from another command into the ConvertTo-HTML command. You will have to use the –Property switch to control which output properties are included in the HTML file and you will have to provide a filename.
To see how this command might be used, think back to the previous section, where we typed Get-Service to create a list of every service that's installed on the system. Now imagine that you want to create an HTML report that lists the name of each service along with its status (regardless of whether the service is running). To do so, you could use the following command:
Get-Service | ConvertTo-HTML –Property Name, Status > C:\services.htm
6: Export-CSV
Just as you can create an HTML report based on PowerShell data, you can also export data from PowerShell into a CSV file that you can open using Microsoft Excel. The syntax is similar to that of converting a command's output to HTML. At a minimum, you must provide an output filename. For example, to export the list of system services to a CSV file, you could use the following command:
Get-Service | Export-CSV c:\service.csv
7: Select-Object
If you tried using the command above, you know that there were numerous properties included in the CSV file. It's often helpful to narrow things down by including only the properties you are really interested in. This is where the Select-Object command comes into play. The Select-Object command allows you to specify specific properties for inclusion. For example, to create a CSV file containing the name of each system service and its status, you could use the following command:
Get-Service | Select-Object Name, Status | Export-CSV c:\service.csv
8: Get-EventLog
You can actually use PowerShell to parse your computer's event logs. There are several parameters available, but you can try out the command by simply providing the –Log switch followed by the name of the log file. For example, to see the Application log, you could use the following command:
Get-EventLog –Log "Application"
Of course, you would rarely use this command in the real world. You're more likely to use other commands to filter the output and dump it to a CSV or an HTML file.
9: Get-Process
Just as you can use the Get-Service command to display a list of all of the system services, you can use the Get-Process command to display a list of all of the processes that are currently running on the system.
10: Stop-Process
Sometimes, a process will freeze up. When this happens, you can use the Get-Process command to get the name or the process ID for the process that has stopped responding. You can then terminate the process by using the Stop-Process command. You can terminate a process based on its name or on its process ID. For example, you could terminate Notepad by using one of the following commands:
Stop-Process –Name notepad
Stop-Process –ID 2668
Keep in mind that the process ID may change from session to session.
11: Get-Acl
This will give you a quick report of your security rights to the specified path (note that it won’t give the share access). That alone is nothing too exciting, as it will report only the single specified path, but if you want to include recursion for the entire path, you can use other strategies. For the same path (N:\Data), you’d use the Get-ChildItem command (cmdlet) within PowerShell, combined with the Get-Acl command. For example:
PS E:\>Get-ChildItem N:\Data -recurse | Get-Acl
This will span the entire N:\Data path and display the ACLs for the contents of the path. What happens here is that the Get-ChildItem provides an inventory of the file system objects, and that collection is passed to Get-Acl to provide the results for each item.
If you want to archive this to a comma-separated variable (CSV) document, you pass “| export-csv c:\filename.csv” at the end of the cmdlet. You can also pass the normal “> C:\filename.txt” to the end of the command to get it exported to a text file. Note that when you use the –recurse option, it does just that and will traverse the entire path you specify. So be careful when doing it across a large volume or over the network.
Saturday, December 11, 2010
Installing IIS 7 on Windows Server 2008
Before going to start lets have a look on IIS in Recent Times
If you think back a few years to IIS 5.0, the future for Microsoft's web server looked rather bleak, because network-savvy worms such as Nimda, Code Red, Code Red II, and their variants were affecting thousands of computers worldwide, and rapidly damaging IIS's reputation. Microsoft introduced the IIS lockdown tool to combat these exploits and, with the release of IIS 6.0, made "locked down" mode settings the default at installation, which helped minimize such security problems, and helped IIS 6.0 recapture a major part of trust that IIS 5.0 lost. No major security disasters have been reported since the release of IIS 6.0.
A market survey (Netcraft Web Server Survey—April 2007 ) indicated that Microsoft's IIS has a 31.13 percent market share, which places it in second position behind the open source Apache Web Server. Another survey by Port80 Software that takes Fortune 1000 companies into consideration reports that IIS has overtaken Apache among Fortune 1000 sites.
If you think back a few years to IIS 5.0, the future for Microsoft's web server looked rather bleak, because network-savvy worms such as Nimda, Code Red, Code Red II, and their variants were affecting thousands of computers worldwide, and rapidly damaging IIS's reputation. Microsoft introduced the IIS lockdown tool to combat these exploits and, with the release of IIS 6.0, made "locked down" mode settings the default at installation, which helped minimize such security problems, and helped IIS 6.0 recapture a major part of trust that IIS 5.0 lost. No major security disasters have been reported since the release of IIS 6.0.
A market survey (Netcraft Web Server Survey—April 2007 ) indicated that Microsoft's IIS has a 31.13 percent market share, which places it in second position behind the open source Apache Web Server. Another survey by Port80 Software that takes Fortune 1000 companies into consideration reports that IIS has overtaken Apache among Fortune 1000 sites.
Figure 1. IIS 7.0 Core Components: IIS 7.0 is composed of three core components.
Now, Microsoft is looking to consolidate IIS 7.0's position as a secure and robust web server.
Now, Microsoft is looking to consolidate IIS 7.0's position as a secure and robust web server.
 | |||||||||||||||||||||||||
| Figure 1. |
IIS 7.0 Core Components
IIS 7.0's core components differ from those in IIS 6.0. IIS 7.0 is made up of three core components as illustrated in Figure 1.
Protocol Listeners: A protocol listener listens to specific requests based on a specific protocol and sends the request to the IIS worker process for processing. Protocol listeners provided with IIS 7.0 include HTTP.sys, NET.TCP, NET.MSMQ and NET.PIPE.
WWW Service: This service acts as a listener adapter for the HTTP.sys protocol listener and monitors the HTTP requests.
Windows Activation Service (WAS): WAS is a new service in IIS 7.0 that manages application pool configuration and worker processes. In IIS 6.0, this responsibility was part of the WWW Service. The shift to a separate core component ensures that developers can use the same process model and configuration for both HTTP and non-HTTP based sites. It is possible to configure the other three protocol listeners (NET.TCP, NET.MSMQ and NET.PIPE) using WAS.
IIS 7.0's core components differ from those in IIS 6.0. IIS 7.0 is made up of three core components as illustrated in Figure 1.
Protocol Listeners: A protocol listener listens to specific requests based on a specific protocol and sends the request to the IIS worker process for processing. Protocol listeners provided with IIS 7.0 include HTTP.sys, NET.TCP, NET.MSMQ and NET.PIPE.
WWW Service: This service acts as a listener adapter for the HTTP.sys protocol listener and monitors the HTTP requests.
Windows Activation Service (WAS): WAS is a new service in IIS 7.0 that manages application pool configuration and worker processes. In IIS 6.0, this responsibility was part of the WWW Service. The shift to a separate core component ensures that developers can use the same process model and configuration for both HTTP and non-HTTP based sites. It is possible to configure the other three protocol listeners (NET.TCP, NET.MSMQ and NET.PIPE) using WAS.
Figure 2. IIS 7.0 Pillars: The figure shows the five major focus areas of IIS 7.0 in which Microsoft made improvements.
For example, when the NET.TCP protocol listener is configured it listens for TCP requests. WAS can also be used to host a Windows Communication Foundation (WCF) based service.
For example, when the NET.TCP protocol listener is configured it listens for TCP requests. WAS can also be used to host a Windows Communication Foundation (WCF) based service.
 |
| Figure 2. |
IIS 7.0 Pillars
Apart from the change in the core components Microsoft made various changes in five major focus areas. These five areas (see Figure 2) form the pillars of IIS 7.0.
Apart from the change in the core components Microsoft made various changes in five major focus areas. These five areas (see Figure 2) form the pillars of IIS 7.0.
Now Installing IIS 7 on Windows Server 2008
Since the IIS web server is not installed by default, the first thing we have to do is install IIS as a role for the server we are working on.
1. Click on Start -> Administrative Tools -> Server Manager
1. Click on Start -> Administrative Tools -> Server Manager
2. In Server Manager scroll down to Roles Summary, and click on Add Roles
3. The Add Roles Wizard starts at this point and warns you that if you are going to add a role to make sure:
The administrator account has a strong password
Network settings, such as static IP, are configured
The latest security updates from Windows Updates are installed
The administrator account has a strong password
Network settings, such as static IP, are configured
The latest security updates from Windows Updates are installed
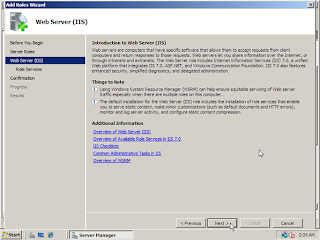
4. Click Next to go the Add Server Role page. Place a checkmark next to Web Server (IIS) and then click on the button Next
5. The next page will give you some basic information on IIS Web Servers and a few links with extra information if needed. Click on the button Next to continue
6. The next window is the Select Role Services. This very important screen will allow you to add only the modules necessary for your planned installation of IIS.
When you choose a module in this screen in the upper right corner you will get more information about what the module is for. For our example we are going to load the following modules:
Static Content – Lets the Web server publish static Web file formats, such as HTML pages and image files.
Use Static Content to publish files on your Web server that users can view using a Web browser.
Default Document – Lets you configure a default file for the Web server to return when users do not specify a file in a URL.
Default Documents make it easier and more convenient for users to reach your Web site.
HTTP Errors – Allows you to customize the error messages returned to users’ browsers when the Web server detects a fault condition.
Use HTTP Errors to provide users with a better user experience when they run up against an error message. Consider providing users with an e-mail address for staff who can help them resolve the error.
HTTP Redirection – Provides support to redirect user requests to a specific destination.
Use HTTP redirection whenever you want customers who are using one URL to actually end up at another URL. This is helpful in many situations, from simply renaming your Web site, to overcoming a domain name that is difficult to spell, or forcing clients to use a secure channel.
HTTP Logging – Provides logging of Web site activity for this server.
When a loggable event, usually an HTTP transaction, occurs, IIS calls the selected logging module, which then writes to one of the logs stored in the files system of the Web server. These logs are in addition to those provided by the operating system.
Request Filtering – Screens all incoming requests to the server and filters these requests based on rules set by the administrator.
Many malicious attacks share common characteristics, like extremely long requests, or requests for an unusual action. By filtering requests, you can attempt to mitigate the impact of these types of attacks.
IIS Management Console – Provides infrastructure to manage IIS 7 by using a user interface.
You can use the IIS management console to manage a local or remote Web server that runs IIS 7. To manage SMTP or FTP, you must install and use the IIS 6 Management Console.
When you choose a module in this screen in the upper right corner you will get more information about what the module is for. For our example we are going to load the following modules:
Static Content – Lets the Web server publish static Web file formats, such as HTML pages and image files.
Use Static Content to publish files on your Web server that users can view using a Web browser.
Default Document – Lets you configure a default file for the Web server to return when users do not specify a file in a URL.
Default Documents make it easier and more convenient for users to reach your Web site.
HTTP Errors – Allows you to customize the error messages returned to users’ browsers when the Web server detects a fault condition.
Use HTTP Errors to provide users with a better user experience when they run up against an error message. Consider providing users with an e-mail address for staff who can help them resolve the error.
HTTP Redirection – Provides support to redirect user requests to a specific destination.
Use HTTP redirection whenever you want customers who are using one URL to actually end up at another URL. This is helpful in many situations, from simply renaming your Web site, to overcoming a domain name that is difficult to spell, or forcing clients to use a secure channel.
HTTP Logging – Provides logging of Web site activity for this server.
When a loggable event, usually an HTTP transaction, occurs, IIS calls the selected logging module, which then writes to one of the logs stored in the files system of the Web server. These logs are in addition to those provided by the operating system.
Request Filtering – Screens all incoming requests to the server and filters these requests based on rules set by the administrator.
Many malicious attacks share common characteristics, like extremely long requests, or requests for an unusual action. By filtering requests, you can attempt to mitigate the impact of these types of attacks.
IIS Management Console – Provides infrastructure to manage IIS 7 by using a user interface.
You can use the IIS management console to manage a local or remote Web server that runs IIS 7. To manage SMTP or FTP, you must install and use the IIS 6 Management Console.
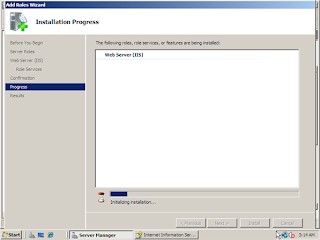
7. Click Next to get to the Confirm Installation Selections screen to verify your chosen settings.
8. Click Install and installation will start
9. After installation you should see the Installation Results page. Click Close to finish the process.
10. In the Server Manager window, under Roles Summary, you should now see Web Server (IIS)
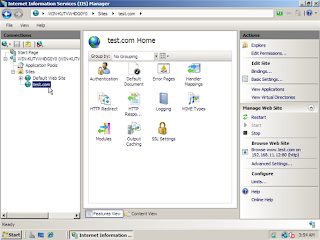
11. Let’s go ahead and open IIS Manager by going to Start -> Administrative Tools -> Internet Information Services (IIS) Manager
12. Once IIS Manager opens, expand out the web server and then expand the Sites folder. Right click on sites and then click on Add Web Site
13. In the Add Web Site window we have some basic information to fill out for a static site:
Site Name – Name of the site, this will be either domain.com or *.domain.com (Where * would represent a sub domain name such as www or blog for example)
Physical Path – The location on the local server that will hold the files for the website. If you did not set this up beforehand you can create a folder through this interface
Type – choose either http or https depending on whether your site will use Secure Socket Layer (SSL) certificate or not
IP Address – From the dropdown you can specify what IP the website should answer on or use the default switch of All Unassigned
Host Name – If you would like this site to respond to other domain names you can put these here
You have now installed IIS 7 and configured a static website. Just place your html files in the directory you specified when creating the site and you are good to go.
Thursday, December 9, 2010
How DNS Recursive Queries Work
The basic concept of DNS name resolution is fairly simple. Every Web site is assigned a unique IP address. In order to access a website, a client needs to know what the site’s IP address is. Of course users don't usually enter an IP address into their Web browser, but rather enter the site's domain name instead. In order to access the requested website, the Web browser must be able to convert the site's domain name into the corresponding IP address. This is where DNS comes into play. The client computer is configured with the address of a preferred DNS server. The requested URL is forwarded to the DNS server, and the DNS server returns the IP address for the requested website. The client is then able to access the requested site.
As you can see, the name resolution process is pretty cut and dry. However, there are countless websites in the world, and new sites are being created every day. It is impossible for your DNS server to know the IP address of every single website. When a DNS server does not know the address for a requested site, it uses one of two methods to determine the site's IP address.
The preferred name resolution method is called recursion. Generally speaking, recursion refers to the process of having the DNS server itself to make queries to other DNS servers on behalf of the client who made the original request. In essence, the DNS server becomes a DNS client. Some administrators prefer to disable recursion for performance reasons. If recursion is disabled, then the DNS server uses a process called iteration to resolve the name request.
Root Hints
If the DNS server does not know the address of the requested site, then it will forward the request to another DNS server. In order to do so, the DNS server must know of the IP address of another DNS server that it can forward the request to. This is the job of root hints. Root hints provided a list of IP addresses of DNS servers that are considered to be authoritative at the root level of the DNS hierarchy.
The good news is that root hints are preconfigured on Windows Server 2003 DNS servers. The root hints are stored in a file named CACHE.DNS that is located in the \Windows\System32\Dns folder. If you would like to see what the root hints file looks like, you can open it in Notepad. As you can see in Figure A, the root hints file is really nothing more than just a text file that pairs root DNS servers with their IP addresses.
Figure A: The root hints file matches root level DNS servers with their IP addresses
Now that I have talked about what the root hints are and what they do, let’s take a look at the recursion process in action. The diagram shown in Figure B illustrates the example that I am about to walk you through.
The process begins when the user enters a URL into their Web browser. For the purpose of this example, let’s assume that the user has entered www.contoso.com as the URL. Upon doing so, the request to resolve the Contoso.com domain into an IP address is passed to the workstation’s preferred DNS server. Often times the preferred DNS server will have already cached the requested record, but for the sake of this example, let’s assume that the preferred DNS server has no information related to CONTOSO.COM.
Assuming that DNS recursion is enabled, the DNS server begins acting as a DNS client and launches a series or iterative queries against other DNS servers. I will discuss the difference between iterative and recursive queries later on, but for now just realize that the process as a whole is considered to be recursive because the client only makes one request to the preferred DNS server.
At any rate, the workstation’s preferred DNS server doesn’t know the IP address of the www.contoso.com Web site, and it doesn’t know the IP address of a DNS server that is authoritative for the Contoso.com domain (and would therefore know the IP address of the www.contoso.com Web site). What the DNS server does know is the IP address to a root level DNS server (thanks to the root hints file). Therefore, the preferred DNS server forwards the request to the root DNS server.
The root DNS server doesn’t have a clue as to the IP address of the www.contoso.com Web server. What it does know is the IP address of a DNS server that is responsible for the .COM domain. The root DNS server returns the IP address of the DNS server responsible for the .COM domain to the preferred DNS server. The preferred DNS server then sends the client’s request to the .COM DNS server. The .COM DNS server doesn’t know the IP address of the www.contoso.com Web site, but it does know the IP address of the DNS server that is authoritative for the Contoso.com domain. The .com domain server returns the IP address of the DNS server that is authoritative for the Contoso.com domain. The client’s preferred DNS server then sends the request to the Contoso.com DNS server, which in turn returns the IP address for the requested Web site. This address is then returned to the client who requested it.
There are two things worth noting in this example. First, as I explained earlier, the client only made a single DNS query. It was completely unaware of the DNS server’s iterative queries on its behalf. Second, the DNS server that is authoritative for the CONTOSO.COM domain would not necessarily be owned by Contoso. Typically, this DNS server would be owned by a Web hosting company and would be authoritative for any sites hosted by the company. That’s why the preferred DNS server can’t skip a step and just give the client the address for the DNS server that is authoritative for the domain; at least not in this case.
If a DNS server is configured to not support recursive queries, then clients will perform iterative queries by default.
If you are interested in obtaining the best performance, then you should configure your DNS server to allow recursive queries. The reason is because if clients are forced to use iterative queries, then they could potentially issue three or four queries to the DNS server for every name resolution request. The DNS server will have to perform all these queries whether recursive or iterative queries are being used, but when recursion is used, most of the name resolution requests are handled by your DNS server and are kept off of your network. This reduces the amount of traffic flowing across the network, thereby improving performance.
Subscribe to:
Comments (Atom)